今天坐牢坐满了八小时,出了三道逆向,一道区块链,帮助我们队拿到了这次比赛的第一名,也算可喜可贺!自己终于不是以前的菜鸡了,遥想去年还啥也不会呢
现在比赛结束了,那就写一下 wp 好咯
PS: 第一次拿到一道困难题的一血,还是很激动的,有一道题目我记得叫做 easyRE,拿了二血是因为吃饭吃到 10 点多才开始做题了,下次一定准时比赛!(下次一定 (●’◡’●))
题目附件: 点击下载
# reverse
# easyRE
这题是 python 逆向,做 python 逆向的方法我感觉挺固定的,就是 pyinstxtractor 解包一下,再把里面的 pyc 转成 py 就可以了
今年年初的时候还对 python 逆向做了些整理呢,可以看看我博客的这篇文章
回到题目,这题呀要怎么刁难我们呢?没错,就是 python3.11
这个版本挺新的,我相信你不管是用 uncompyle6 还是 pycdc 还是在线网站,应该都会遇到反编译失败的情况,那么这个时候我们该怎么办呢?
其实是有方法的,首先,我们可以用如下的 python 代码得到这个 pyc 的字节码
import dis | |
import marshal | |
with open('easyRE.pyc', 'rb') as f: | |
f.seek(16) | |
dis.dis(marshal.load(f)) |
0 0 RESUME 0 | |
1 2 LOAD_CONST 0 (0) | |
4 LOAD_CONST 1 (None) | |
6 IMPORT_NAME 0 (random) | |
8 STORE_NAME 0 (random) | |
3 10 PUSH_NULL | |
12 LOAD_NAME 0 (random) | |
14 LOAD_ATTR 1 (Random) | |
24 LOAD_CONST 2 (322376503) | |
26 PRECALL 1 | |
30 CALL 1 | |
40 STORE_NAME 2 (r) | |
6 42 PUSH_NULL | |
44 LOAD_NAME 3 (input) | |
46 LOAD_CONST 3 ('Enter your flag: ') | |
48 PRECALL 1 | |
52 CALL 1 | |
62 LOAD_METHOD 4 (encode) | |
84 PRECALL 0 | |
88 CALL 0 | |
98 STORE_NAME 5 (pt) | |
8 100 LOAD_CONST 4 (b'\x8b\xcck\xd3\xed\x96\xffFb\x06r\x085\x82\xbc \xb2\xde)p\x88Q`\x1bf\x18\xb6QUSw\x10\xcd\xd9\x13A$\x86\xe5\xcd\xd9\xff') | |
102 STORE_NAME 6 (ct) | |
10 104 BUILD_LIST 0 | |
106 STORE_NAME 7 (buf) | |
12 108 LOAD_NAME 5 (pt) | |
110 GET_ITER | |
>> 112 FOR_ITER 46 (to 206) | |
114 STORE_NAME 8 (b) | |
13 116 LOAD_NAME 7 (buf) | |
118 LOAD_METHOD 9 (append) | |
140 LOAD_NAME 2 (r) | |
142 LOAD_METHOD 10 (randint) | |
164 LOAD_CONST 0 (0) | |
166 LOAD_CONST 5 (255) | |
168 PRECALL 2 | |
172 CALL 2 | |
182 LOAD_NAME 8 (b) | |
184 BINARY_OP 12 (^) | |
188 PRECALL 1 | |
192 CALL 1 | |
202 POP_TOP | |
204 JUMP_BACKWARD 47 (to 112) | |
15 >> 206 PUSH_NULL | |
208 LOAD_NAME 11 (bytes) | |
210 LOAD_NAME 7 (buf) | |
212 PRECALL 1 | |
216 CALL 1 | |
226 LOAD_NAME 6 (ct) | |
228 COMPARE_OP 2 (==) | |
234 POP_JUMP_FORWARD_IF_TRUE 2 (to 240) | |
236 LOAD_ASSERTION_ERROR | |
238 RAISE_VARARGS 1 | |
17 >> 240 PUSH_NULL | |
242 LOAD_NAME 12 (print) | |
244 LOAD_CONST 6 ('Correct!') | |
246 PRECALL 1 | |
250 CALL 1 | |
260 POP_TOP | |
262 LOAD_CONST 1 (None) | |
264 RETURN_VALUE |
到了这一步其实就可以做题了,但是或许有小伙伴一看到字节码头都大了
这时就要请出我们神奇的 chatgpt 了,网址在这里 https://chat.openai.com/
直接把字节码丢给他然后说:给我转成 py 代码!
然后 chatgpt 就会刷刷刷的给出 py 源代码
import random | |
r = random.Random(322376503) | |
pt = input('Enter your flag: ').encode() | |
ct = b'\x8b\xcck\xd3\xed\x96\xffFb\x06r\x085\x82\xbc \xb2\xde)p\x88Q`\x1bf\x18\xb6QUSw\x10\xcd\xd9\x13A$\x86\xe5\xcd\xd9\xff' | |
buf = [] | |
for b in pt: | |
buf.append(r.randint(0, 255) ^ b) | |
assert bytes(buf) == ct | |
print('Correct!') |
这一看随机数种子都固定了,那随机数其实就不随机了
基于题目的代码改一改就是 flag 了
import random | |
r = random.Random(322376503) | |
pt = input('Enter your flag: ').encode() | |
ct = b'\x8b\xcck\xd3\xed\x96\xffFb\x06r\x085\x82\xbc \xb2\xde)p\x88Q`\x1bf\x18\xb6QUSw\x10\xcd\xd9\x13A$\x86\xe5\xcd\xd9\xff' | |
for k in ct: | |
print(chr(r.randint(0, 255) ^ k),end='') | |
# flag{69858b56-4987-438f-a02c-5ab5c09e5138} |
# gotots
这题是一道 go 语言的逆向题,做这种 go 语言的题目,其实把那些函数都给复原就相当好做了 (做 go 逆向找不到 main_main 就好像…emmm 想不出来用什么比喻好了 qwq)
所以我们首先要做的是还原函数名称,用这个 ida 脚本就可以了 https://github.com/renshareck/IDAGolangHelper_SupportGo1.20
然后按照下图的流程依次点击按钮
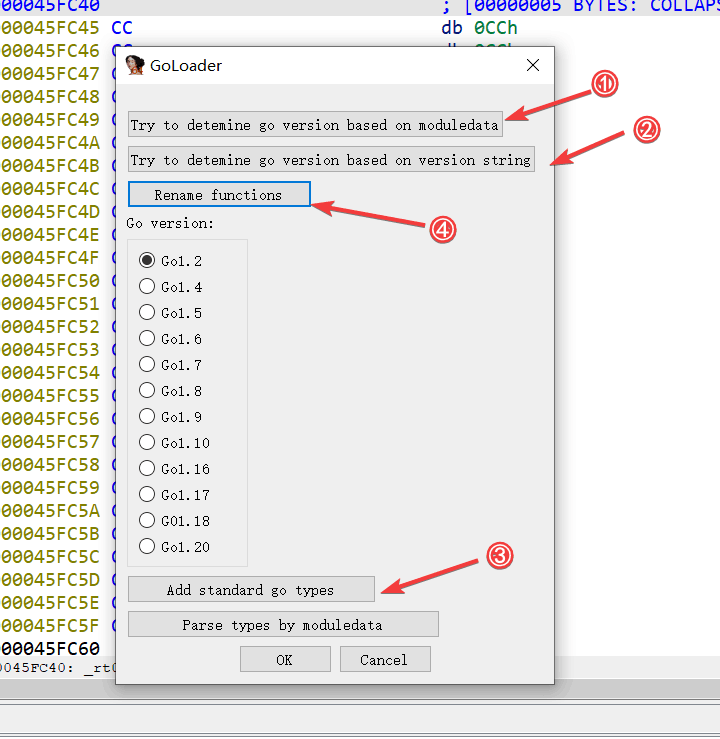
还原之后发现是梅森旋转算法随机数生成器,这是一个伪随机数生成器,每次异或的值都是一样的
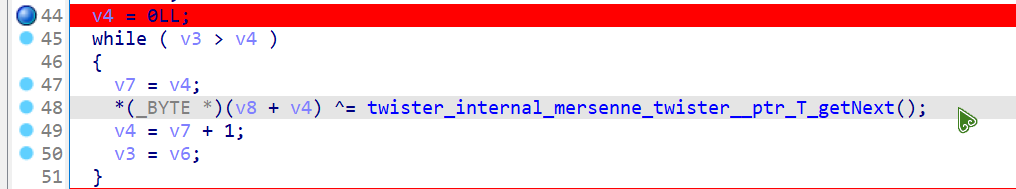
那就随便输入一个字符串比如我这里输入的是 0000000000000000000000000000000000000000000000 , 然后打个断点把异或后的那个数组复制下来,然后再去异或后面要比较的数组,这样就可以拿到 flag 了
挺简单的题目,直接给 exp 吧
testinput = "0000000000000000000000000000000000000000000000" | |
byte = [0x67, 0x88, 0xBE, 0x8C, 0x79, 0xAB, 0x7C, 0xB7, 0x5F, 0xD3, 0x24, 0xD0, 0x16, 0xF0, 0x02, 0x8D, 0x5C, 0xF7, 0xB5, 0x16, 0xD2, 0x69, 0xDE, 0xA6, 0xE1, 0x5F, 0xA1, 0xA5, 0x7F, 0x6C, 0x78, 0x70, 0x76, 0x88, 0x75, 0x2E, 0x2F, 0x30, 0x99, 0x61, 0x5A, 0xD1, 0xBF, 0x71, 0x7A, 0x4E] | |
key = [0x35, 0x8C, 0xEB, 0x85, 0x2C, 0xFA, 0x2D, 0xB1, 0x42, 0x82, 0x27, 0xD0, 0x10, 0xED, 0x06, 0x8E, 0x0D, 0xFE, 0xA8, 0x1E, 0x81, 0x3C, 0x8A, 0xBB, 0xB7, 0x0B, 0xF4, 0xF0, 0x7C, 0x6B, 0x70, 0x26, 0x71, 0x8B, 0x73, 0x7D] | |
for i in range(len(key)): | |
print(chr(ord(testinput[i])^byte[i]^key[i]),end='')# b4e9eaa6-a306-43a9-8ced-fdee378f736c |
# multi-universe
这题拿了一血 (没想到我也有拿一血的一天!肯定是大佬们还没有发力唔)
这题呀也是 go 逆向,不过就是和 c 代码交叉编译了一下
同样,第一步还是恢复函数名称,可以用这个 ida 脚本 https://github.com/0xjiayu/go_parser , 然后就可以了,这里运行脚本之后可能会卡住,不过没关系,cancel 掉脚本,函数名称一样可以恢复过来
之后呐就是随便输入一个 40 位的字符串,然后在输入后的字符串的内存地址处打个硬件断点,动态调试之后断点一路触发下去,跟到这个函数 sub_7FF631BCF2E0 , 我觉得你有可能找不到这个函数因为动态调试后基址可能不一样,我的基址是 0x7FF631B30000 , 如果你找不到加密函数的话在 ida 里面换成我这个基址就可以找得到了 (什么你不会换基址?!跟着我来:在 ida 左上角找到 Edit -> Segments -> Rebase program 然后把我这个基址输进去就可以了)
这个函数的伪代码如下
unsigned int *__fastcall sub_7FF631BCF2E0(void *a1, __int64 a2, unsigned int *a3, _DWORD *a4, size_t a5, int a6) | |
{ | |
unsigned int *v7; // rcx | |
unsigned __int64 v8; // rsi | |
unsigned int *result; // rax | |
unsigned int *v10; // r8 | |
unsigned int v11; // r9d | |
int v12; // ecx | |
unsigned int v13; // ecx | |
int v14; // edx | |
unsigned int v15; // edx | |
int v16; // ecx | |
unsigned int v17; // ecx | |
int v18; // edx | |
unsigned int v19; // edx | |
int v20; // ecx | |
unsigned int v21; // ecx | |
int v22; // edx | |
unsigned int v23; // edx | |
int v24; // ecx | |
unsigned int v25; // ecx | |
int v26; // edx | |
unsigned int v27; // edx | |
int v28; // ecx | |
unsigned int v29; // ecx | |
int v30; // edx | |
unsigned int v31; // edx | |
int v32; // ecx | |
unsigned int v33; // ecx | |
int v34; // edx | |
unsigned int v35; // edx | |
int v36; // ecx | |
unsigned int v37; // ecx | |
int v38; // edx | |
unsigned int v39; // edx | |
unsigned int v40; // r9d | |
__m128i v41; // xmm5 | |
int v42; // edx | |
unsigned int v43; // edx | |
int v44; // ecx | |
v7 = a3; | |
v8 = a6; | |
if ( a3 != (unsigned int *)a5 ) | |
v7 = (unsigned int *)memcpy(a1, (const void *)a6, a5); | |
result = v7; | |
v10 = (unsigned int *)((char *)v7 + (v8 & 0xFFFFFFFFFFFFFFF8LL)); | |
if ( v8 >> 3 ) | |
{ | |
do | |
{ | |
v11 = *a4 ^ *result; | |
*result = v11; | |
v12 = result[1] ^ (a4[(unsigned __int8)v11 + 786] | |
+ (a4[BYTE1(v11) + 530] ^ (a4[HIBYTE(v11) + 18] + a4[BYTE2(v11) + 274]))); | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v12), _mm_cvtsi32_si128(v11)).m128i_u64[0]; | |
v13 = a4[1] ^ v12; | |
*result = v13; | |
v14 = v11 ^ (a4[(unsigned __int8)v13 + 786] | |
+ (a4[BYTE1(v13) + 530] ^ (a4[HIBYTE(v13) + 18] + a4[BYTE2(v13) + 274]))); | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v14), _mm_cvtsi32_si128(v13)).m128i_u64[0]; | |
v15 = a4[2] ^ v14; | |
*result = v15; | |
v16 = (a4[(unsigned __int8)v15 + 786] + (a4[BYTE1(v15) + 530] ^ (a4[HIBYTE(v15) + 18] + a4[BYTE2(v15) + 274]))) ^ v13; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v16), _mm_cvtsi32_si128(v15)).m128i_u64[0]; | |
v17 = a4[3] ^ v16; | |
*result = v17; | |
v18 = (a4[(unsigned __int8)v17 + 786] + (a4[BYTE1(v17) + 530] ^ (a4[HIBYTE(v17) + 18] + a4[BYTE2(v17) + 274]))) ^ v15; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v18), _mm_cvtsi32_si128(v17)).m128i_u64[0]; | |
v19 = a4[4] ^ v18; | |
*result = v19; | |
v20 = (a4[(unsigned __int8)v19 + 786] + (a4[BYTE1(v19) + 530] ^ (a4[HIBYTE(v19) + 18] + a4[BYTE2(v19) + 274]))) ^ v17; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v20), _mm_cvtsi32_si128(v19)).m128i_u64[0]; | |
v21 = a4[5] ^ v20; | |
*result = v21; | |
v22 = (a4[(unsigned __int8)v21 + 786] + (a4[BYTE1(v21) + 530] ^ (a4[HIBYTE(v21) + 18] + a4[BYTE2(v21) + 274]))) ^ v19; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v22), _mm_cvtsi32_si128(v21)).m128i_u64[0]; | |
v23 = a4[6] ^ v22; | |
*result = v23; | |
v24 = (a4[(unsigned __int8)v23 + 786] + (a4[BYTE1(v23) + 530] ^ (a4[HIBYTE(v23) + 18] + a4[BYTE2(v23) + 274]))) ^ v21; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v24), _mm_cvtsi32_si128(v23)).m128i_u64[0]; | |
v25 = a4[7] ^ v24; | |
*result = v25; | |
v26 = (a4[(unsigned __int8)v25 + 786] + (a4[BYTE1(v25) + 530] ^ (a4[HIBYTE(v25) + 18] + a4[BYTE2(v25) + 274]))) ^ v23; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v26), _mm_cvtsi32_si128(v25)).m128i_u64[0]; | |
v27 = a4[8] ^ v26; | |
*result = v27; | |
v28 = (a4[(unsigned __int8)v27 + 786] + (a4[BYTE1(v27) + 530] ^ (a4[HIBYTE(v27) + 18] + a4[BYTE2(v27) + 274]))) ^ v25; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v28), _mm_cvtsi32_si128(v27)).m128i_u64[0]; | |
v29 = a4[9] ^ v28; | |
*result = v29; | |
v30 = (a4[(unsigned __int8)v29 + 786] + (a4[BYTE1(v29) + 530] ^ (a4[HIBYTE(v29) + 18] + a4[BYTE2(v29) + 274]))) ^ v27; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v30), _mm_cvtsi32_si128(v29)).m128i_u64[0]; | |
v31 = a4[10] ^ v30; | |
*result = v31; | |
v32 = (a4[(unsigned __int8)v31 + 786] + (a4[BYTE1(v31) + 530] ^ (a4[HIBYTE(v31) + 18] + a4[BYTE2(v31) + 274]))) ^ v29; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v32), _mm_cvtsi32_si128(v31)).m128i_u64[0]; | |
v33 = a4[11] ^ v32; | |
*result = v33; | |
v34 = (a4[(unsigned __int8)v33 + 786] + (a4[BYTE1(v33) + 530] ^ (a4[HIBYTE(v33) + 18] + a4[BYTE2(v33) + 274]))) ^ v31; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v34), _mm_cvtsi32_si128(v33)).m128i_u64[0]; | |
v35 = a4[12] ^ v34; | |
*result = v35; | |
v36 = (a4[(unsigned __int8)v35 + 786] + (a4[BYTE1(v35) + 530] ^ (a4[HIBYTE(v35) + 18] + a4[BYTE2(v35) + 274]))) ^ v33; | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v36), _mm_cvtsi32_si128(v35)).m128i_u64[0]; | |
v37 = a4[13] ^ v36; | |
*result = v37; | |
result += 2; | |
v38 = (a4[(unsigned __int8)v37 + 786] + (a4[BYTE1(v37) + 530] ^ (a4[HIBYTE(v37) + 18] + a4[BYTE2(v37) + 274]))) ^ v35; | |
*((_QWORD *)result - 1) = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v38), _mm_cvtsi32_si128(v37)).m128i_u64[0]; | |
v39 = a4[14] ^ v38; | |
*(result - 2) = v39; | |
v40 = v39; | |
v41 = _mm_cvtsi32_si128(v39); | |
v42 = v37 ^ (a4[(unsigned __int8)v39 + 786] | |
+ ((a4[HIBYTE(v39) + 18] + a4[BYTE2(v39) + 274]) ^ a4[BYTE1(v39) + 530])); | |
*((_QWORD *)result - 1) = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v42), v41).m128i_u64[0]; | |
v43 = a4[15] ^ v42; | |
*(result - 2) = v43; | |
v44 = v40 ^ (a4[(unsigned __int8)v43 + 786] | |
+ (a4[BYTE1(v43) + 530] ^ (a4[HIBYTE(v43) + 18] + a4[BYTE2(v43) + 274]))); | |
*((_QWORD *)result - 1) = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v43), _mm_cvtsi32_si128(v44)).m128i_u64[0]; | |
*(result - 1) = a4[16] ^ v44; | |
*(result - 2) = a4[17] ^ v43; | |
} | |
while ( result != v10 ); | |
} | |
return result; | |
} |
这个加密也是有迹可循的,就是异或来~异或去,你可以把这个加密看成很多下方代码块的重复
v11 = *a4 ^ *result; | |
*result = v11; | |
v12 = result[1] ^ (a4[(unsigned __int8)v11 + 786] | |
+ (a4[BYTE1(v11) + 530] ^ (a4[HIBYTE(v11) + 18] + a4[BYTE2(v11) + 274]))); | |
*(_QWORD *)result = _mm_unpacklo_epi32(_mm_cvtsi32_si128(v12), _mm_cvtsi32_si128(v11)).m128i_u64[0]; |
这个算法要注意 (unsigned __int8) , BYTE1 , HIBYTE , BYTE2 表示的含义
假设 v11=0x12345678 , 那么
(unsigned __int8)v11 = 0x78BYTE1(v11) = 0x56HIBYTE(v11) = 0x12BYTE2(v11) = 0x34
while 循环最后的两个异或也不能忽略
*(result - 1) = a4[16] ^ v44; | |
*(result - 2) = a4[17] ^ v43; |
提醒一点,当你在 result 数组的内存地址打下硬件断点后,会发现这个函数执行完毕后,后面还有一个小型的加密
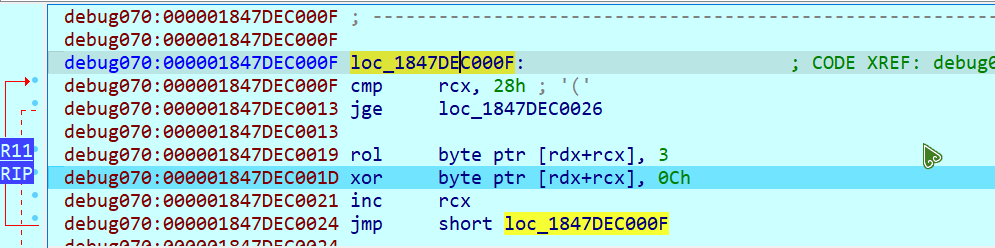
记得也要把这个循环左移三位再异或也体现到 exp 里面去
那就可以写出 exp 来了
import ctypes | |
import binascii | |
def deal_last_rev(hex_num): | |
# hex_num = 0x9DDC359E | |
byte1 = (hex_num >> 24) & 0xFF | |
byte2 = (hex_num >> 16) & 0xFF | |
byte3 = (hex_num >> 8) & 0xFF | |
byte4 = hex_num & 0xFF | |
byte1 = ctypes.c_uint8(byte1) | |
byte1.value ^= 0x0C | |
# print(bin(byte1.value)) | |
byte1.value = ((byte1.value<<5)&0xff)|((byte1.value>>3)&0xff) | |
# print(bin(byte1.value)) | |
byte2 = ctypes.c_uint8(byte2) | |
byte2.value ^= 0x0C | |
byte2.value = ((byte2.value<<5)&0xff)|((byte2.value>>3)&0xff) | |
byte3 = ctypes.c_uint8(byte3) | |
byte3.value ^= 0x0C | |
byte3.value = ((byte3.value<<5)&0xff)|((byte3.value>>3)&0xff) | |
byte4 = ctypes.c_uint8(byte4) | |
byte4.value ^= 0x0C | |
byte4.value = ((byte4.value<<5)&0xff)|((byte4.value>>3)&0xff) | |
result = (byte1.value << 24) | (byte2.value << 16) | (byte3.value << 8) | byte4.value | |
return result | |
def rrev(hex_num): | |
byte1 = (hex_num >> 24) & 0xFF | |
byte2 = (hex_num >> 16) & 0xFF | |
byte3 = (hex_num >> 8) & 0xFF | |
byte4 = hex_num & 0xFF | |
result = (byte4 << 24) | (byte3 << 16) | (byte2 << 8) | byte1 | |
return result | |
a4 = [0x2FE994E0, 0xC11E954B, 0xF00E449D, 0xDA7858A1, 0xCEF89B0A, 0xB06F5FD9, 0x32646DF2, 0x3D31F55A, 0xE90EC568, | |
0xF69C53B7, 0x3F2C9C44, 0x6DD31BC7, 0xF4AF32ED, 0x4381F9C7, 0x26EB634F, 0xE5FBA3CF, 0xAB36B7FB, 0xB295A35B, | |
0x732F94D5, 0xEEC6C173, 0x572989EB, 0xCB9DDFD9, 0xAF9F559B, 0xFC9A4D99, 0xE14B9327, 0x3A04B794, 0x588C93A9, | |
0xB75B93DF, 0xFC906662, 0x7043911C, 0x71F1F968, 0xAEC02345, 0x642C0A73, 0xE92FD10A, 0xF749BE48, 0x02C776F8, | |
0x78D847B6, 0xD9D395EA, 0xC091094D, 0x5ED1A899, 0x8535B464, 0xC9B571E4, 0xD5974F29, 0x69BF7AC2, 0x78862ED1, | |
0xAEA837DD, 0x4D8BF9B9, 0x358766D5, 0x0194484B, 0xB2C46C77, 0xA5B3F500, 0x21B29753, 0xC8BE07B5, 0x9B982150, | |
0xAAB0F261, 0xC54587BA, 0x5FE3F7A2, 0xB94325DF, 0x814B1991, 0x05A7CBC5, 0xC01E7032, 0x2D802ED9, 0xF920C022, | |
0xDC7AAE97, 0x3904A61F, 0x8A725DE7, 0x9E49A196, 0xF7AE5DF0, 0x19EB724A, 0x03FB7CF7, 0x2F9234AF, 0x72006306, | |
0x9123B54C, 0xB8164574, 0x69438E25, 0xD56F49D2, 0x681CB159, 0x8CDADDF4, 0xFCE82189, 0x50A905D4, 0x9386E52A, | |
0xCACC2368, 0x38B3A6A3, 0x3CA0DF37, 0xF51D7DD5, 0x24242D86, 0x7F8D441B, 0xD6E5BBA6, 0x263CBCD8, 0xE3ADDED7, | |
0x6D543F5E, 0x4716D72F, 0x2799B4E3, 0xA80B339E, 0x2A9A3565, 0x812ECA54, 0x58A9D96E, 0xCF3ACC39, 0x2777DC51, | |
0x520F1EF8, 0xF4A2399E, 0x0BB7A943, 0x9BB2287A, 0x074C750B, 0xE89F260C, 0xF39494C9, 0x62154805, 0x2869BB07, | |
0x71D3C65F, 0x83F883C6, 0x179A9696, 0xD53E6014, 0x28A45FBB, 0x565C9FD2, 0x4CC74F44, 0x50FD664A, 0x0789A88D, | |
0x7454AE55, 0x4AD93102, 0xC4C64C97, 0x146A16C5, 0xA6337621, 0x601474DD, 0xD9CCBFA2, 0xD628928F, 0xEC0EF727, | |
0x4E728F4C, 0x6D394E22, 0x23252BC3, 0x410DB272, 0x60C5467F, 0x28C58C78, 0x45B98E47, 0x2D453756, 0x9FC502FE, | |
0x2FAAA75C, 0xFECC881C, 0xC98742BD, 0x18FAB5A0, 0x96A2691B, 0x265C4ABE, 0x22E5221D, 0x79F147B5, 0xA4963A5A, | |
0x38A53CE1, 0xC5899BDF, 0xAFBEDE5A, 0xED2EF97D, 0x212A53AC, 0x2E7141D6, 0x2FCF2D57, 0xEFB9869F, 0xD4665961, | |
0x231BB16A, 0x12EF4976, 0x7DAF240E, 0x3B96114A, 0xD27BB394, 0x357215CD, 0xA4AAEF55, 0x17E76552, 0x6F57C2DD, | |
0x83ED82E0, 0xCAABAEA5, 0xE7F5B748, 0xAB0E7982, 0x54435C78, 0x366A7F66, 0x7F94D113, 0x0D96FFBB, 0x2A795FF7, | |
0x2641EF7A, 0x73C2CB56, 0x701792C4, 0x1CCD9DF5, 0x156882B1, 0x888343F4, 0xE22DB762, 0x9E4CCB4B, 0x21517A50, | |
0x072F9091, 0x3E06A3DE, 0x311619DD, 0xA0AB192D, 0x5F0D5CF1, 0xF05FCFEA, 0xE36DEA48, 0x3FC54006, 0xBA8849A7, | |
0xB32DC878, 0xC1FEF774, 0xE34A6EDB, 0x770A2D0D, 0xCDF8D3DC, 0x7EBE066A, 0x603CD5BC, 0x4C6B5E7B, 0x12E80727, | |
0xFB69C765, 0x87A42B29, 0xE73A641F, 0xD586AB9B, 0x3BB112B3, 0x59AF1110, 0x1F6FACFB, 0x52597DF3, 0x28EF38D8, | |
0xBA0432C7, 0x958FDEA9, 0x68678326, 0x2161A62B, 0x44C8C4A0, 0xB1D7A078, 0x205CA9E3, 0xD4B8C306, 0x63F9157D, | |
0x4AEDA561, 0xFB84C9D6, 0xD8988F07, 0xF21A9841, 0xF4E71FB2, 0x63232B2E, 0x6EBA9AFE, 0x2DAFE02C, 0xDCC6655E, | |
0xFDB3B0DE, 0x044C3EAD, 0x10468B3E, 0xDA71D948, 0x6BACCBE4, 0x9A7844FC, 0xDF7FE345, 0xCB06712C, 0x034AC145, | |
0x510E9532, 0x71EAFBC2, 0x44433456, 0xCB01159D, 0x4A1957DD, 0x73C8DF17, 0xC8DB9516, 0x1ADB1906, 0x676BCEC1, | |
0x08DAC3C4, 0x3CAD32A1, 0xD737D4F3, 0x20ACDE94, 0xAB6D02F3, 0x506E5C37, 0xEDF08E37, 0x668C8DD5, 0xEA33C67D, | |
0x35308BA4, 0x67F0A8BA, 0x166546B5, 0x38D06E3F, 0x68159FEC, 0x1CEC8FA1, 0x9917E8B9, 0x376C0882, 0x9AADF201, | |
0x42DACD9C, 0x37663273, 0x51639640, 0x3CA96C41, 0xFD7E97CE, 0x174CAD5D, 0xA7A5F995, 0x2C36EB62, 0x7AFCFC30, | |
0x23DC7E23, 0xD742DA78, 0x03D27CB1, 0x7E9EDC0A, 0x6A0FB256, 0x4FCDB0EF, 0x26CAB2D4, 0x095BA999, 0x839CB8C4, | |
0x288AE59D, 0x1F033326, 0x5E8761CF, 0x0648ED4C, 0x98C49A53, 0xE3C0390D, 0xAD642407, 0xBD269591, 0x32A2E629, | |
0xE3122457, 0x5D73ED1C, 0x33A26E04, 0x2E67DE60, 0x6F2B18E3, 0x4558EADB, 0xDBA1D8B3, 0x9CADF7B5, 0x5FFBB4EF, | |
0x805AD7D1, 0xFF84E641, 0x4D49B28B, 0x2A28EA66, 0x7BC6FA3C, 0x266731FC, 0x3AB4D8DA, 0xB43EB68E, 0x9C4D6F43, | |
0x1CCE439F, 0xB625A0CE, 0x4B78AF95, 0xD06A3FF7, 0x5C8A2078, 0xFD9FA69D, 0x7BF98A71, 0xEE90B86D, 0xA442A73A, | |
0xB5A4A212, 0xA8E481F6, 0x4C6FD0BD, 0xA7706FB4, 0x3569127F, 0x59DFADB6, 0x2AB4FB23, 0x3604808A, 0xF3779794, | |
0xAA5A7EDF, 0x2ECF97BA, 0x969504A5, 0xCD05B77F, 0x5321DB1D, 0xD8BABA9C, 0x7A97EF53, 0x37231A53, 0x366BFEC5, | |
0x9BD96A49, 0x5A6C7F46, 0xE47BD143, 0x13FD722B, 0xF9A52E09, 0x6420A5BC, 0x8A8BB90C, 0x8234235E, 0x215EC40C, | |
0x46790597, 0x825EA222, 0xB783D749, 0x24A8815F, 0x2F74A78E, 0xD9E403D4, 0x63E17B10, 0xB6226CEF, 0x0E0F4381, | |
0xCA7D3369, 0x728C9C6B, 0xB14ECC63, 0x991A0F0E, 0xB0422615, 0x4C2FD823, 0x3302908B, 0xBAAF7739, 0x357EF5BC, | |
0x4CC6687F, 0xDD2F23B7, 0xA3AC1329, 0xC167B555, 0xE1F9B87B, 0x2B65D3B4, 0x4368817B, 0x03DAF56A, 0x9AE59AB9, | |
0xF5EAC7EE, 0xB36417A7, 0xF8FC224A, 0xA7E519FE, 0x8637329C, 0xB21461FD, 0xAED97750, 0x8744167F, 0x4669E638, | |
0x4E1B3B1A, 0xD377B3F7, 0xF514B3B6, 0x707A415C, 0x0AB652F0, 0xBC513A6D, 0x4FCE3F92, 0x96CBEE70, 0x31351026, | |
0xD37A9F73, 0x4DD00F9E, 0x047C1B22, 0x071DF745, 0x3A7697BE, 0xE24EDC03, 0x37233D96, 0x02373DD2, 0x26396C2B, | |
0x2229D430, 0x770CE3E3, 0xDE942CD0, 0x3F79B030, 0x5149DB45, 0x67FFE1C5, 0x78F66A56, 0x0E2313EA, 0xE13FE0C7, | |
0xA0C51FC4, 0xC11D9CA7, 0x709A60B2, 0x32EC174F, 0xC8CA5D05, 0x3351393B, 0x57846D6C, 0x22834834, 0x0FFA5DFE, | |
0x95DB516A, 0xC61E38F0, 0x15A3EE21, 0x4A587F75, 0x5BE749D7, 0xBBF167D7, 0x7334E07D, 0x09606180, 0x8BB6560E, | |
0xD35FFC0F, 0x34DCFBCC, 0x3E98BA62, 0x8A33C7EF, 0x19763E8B, 0x01FA474D, 0x529A6743, 0xF65D218C, 0xE0D70194, | |
0xBC879FCC, 0xE9DB6228, 0x07D566B6, 0x4C1B0D84, 0x945ABD96, 0xD1196C6E, 0x81EE67CC, 0xAD1721AE, 0xC987453F, | |
0x063CEB9F, 0xB27F0A73, 0xB5997727, 0x69D5B851, 0x02F7D0A1, 0x074F31CB, 0x53088D46, 0xBF2D83C4, 0x6C75BC86, | |
0x3B888596, 0x2EA614FE, 0x9E16DD01, 0xED1F5D7C, 0x9916A175, 0xD610A890, 0x7DF08F91, 0x435A4D29, 0xB7B5E450, | |
0x76FA8AAC, 0x050ADB83, 0x9CF8C712, 0xF08E8112, 0x9BAC9884, 0x5568DDC3, 0x4BE91FFE, 0x5B230AA2, 0x6BFDA2E9, | |
0xD26E1DFB, 0xF24668C7, 0x5464086A, 0xFFBB1CF3, 0x13313B25, 0x04D2D867, 0x5C47617D, 0x33A3150D, 0x007C3A17, | |
0x87DF6435, 0x8937F0DF, 0x3A707415, 0x3B2CFAE3, 0xC46C894B, 0xA0BE1104, 0xE2BECABC, 0xE42FDEED, 0x21913FA9, | |
0x1C30A346, 0x12758853, 0x57143736, 0x67E8119A, 0xD49D2036, 0x56AC8659, 0xA2DBB273, 0xFAB5912A, 0x75903A11, | |
0x9F1CC55A, 0x12554844, 0x658813AD, 0xBA08D453, 0x93AD4948, 0xEDDC0E10, 0xE25B6FD1, 0x9DF9AFCC, 0x2E98B6A2, | |
0x731A29AB, 0x930F9D67, 0x4771AC8E, 0xDFE58864, 0x4B572200, 0x67C22CE4, 0x1C5CB393, 0x7F18DC62, 0xBAFE6E58, | |
0x8F157813, 0xEDBB60E4, 0x17CC1A84, 0x5F7D0A2E, 0x64091858, 0x7BAF9420, 0xE1C89AA7, 0x525DF47C, 0x12CDE243, | |
0x0E25EC45, 0x9B36BC9F, 0x78B1715D, 0x962F9E9F, 0x7C18C853, 0xF1A8E5E3, 0x3C7FA3EE, 0xC119713F, 0x499EBAED, | |
0x71E46262, 0x9E42E3EF, 0x46C80691, 0xE4B23574, 0xF5BABE2B, 0x5B2C9A33, 0x296DFA2B, 0x9CEC6D11, 0x4B8A27BF, | |
0xC1C9FAE3, 0xFE7DCB7D, 0x58EBCAFE, 0xAFC4FB8C, 0xC277EB5C, 0x3176F3AC, 0xBC6DD7C1, 0x92E42C52, 0x18381B68, | |
0xB6ADFC6F, 0x7F477C10, 0xD43CCEDC, 0x1FA5633B, 0x3C8E5DF4, 0x2B48DCD9, 0x8C326067, 0x567DDE4E, 0x135E0F94, | |
0x765226D0, 0x5E1E4408, 0xEEAE88D4, 0x082C696B, 0x80A41500, 0xF3964793, 0x8589F6BA, 0x52B1E0B9, 0xBDA9EED6, | |
0x5542F81B, 0xAF48CA37, 0x1D014D51, 0xE38EA0E3, 0x1AA9456C, 0x21F5284A, 0xFB3B912D, 0xFCBCE946, 0xD54DB4A9, | |
0xE0EB8A10, 0x71B621D0, 0x0926496F, 0x79BBECDF, 0xC2E04AB2, 0x5C3B27A9, 0x20521B1E, 0xF644B47A, 0x918AE499, | |
0x2A1957E3, 0xA99F9DE2, 0x0CB70521, 0xAA2B2092, 0xC9F228EA, 0x6D683F3E, 0xE3F41AE0, 0x464A1769, 0x9C03F898, | |
0xDE9509F6, 0x732AEA1F, 0x146E5313, 0x8721E289, 0xAD6C48EF, 0x920B4228, 0x00FB935C, 0x0071D1DE, 0x7677932B, | |
0xACC60C24, 0x2B2C304C, 0x2E8661EC, 0xC7044B76, 0x64A3E5C6, 0x9684B218, 0x708EE6E2, 0x5DC74CA9, 0xE4BC1927, | |
0x22418B42, 0xE8E3D9C2, 0x5466078D, 0xBD66ED30, 0xDDE518BC, 0x6A6C32B9, 0x5BD25D34, 0xF7AA086E, 0xB8B683D5, | |
0x6EDD605B, 0xDA373814, 0xC26A335E, 0xA1077DB1, 0xEE9B3078, 0x2B2A915D, 0xCEED5305, 0x78E15F73, 0x1F9CFEBC, | |
0xF25A97FF, 0xFD36081E, 0xF60AC26D, 0xFE0C1AD0, 0x130FF5E5, 0xE1B8485A, 0x2A6200A2, 0xE71DDBAF, 0x157EE174, | |
0x8AC40711, 0xDAD02A4F, 0xA6AF6F7C, 0x9AB6D314, 0xF51E249C, 0xB18B878B, 0xE0547C50, 0x2202349F, 0x0F007C35, | |
0xF96A3AC7, 0x070EC924, 0x8CAFD12E, 0x93AAD3F8, 0x76CC52D8, 0x9C255CE4, 0x34F401D0, 0x6B479EAF, 0x7D45F765, | |
0xEBD846DB, 0xB4660D11, 0x66675434, 0xEE4E8855, 0x3C9898DA, 0xCCC78B80, 0x49E7F697, 0x8C8C25E1, 0xD8CBDCD6, | |
0xEE8D2953, 0x3F0F1EAA, 0xB3974DB4, 0xEEE04672, 0xCF3BEB72, 0x7322BCAD, 0x2052FEE1, 0x02961CC1, 0x5EBF91D2, | |
0x84B3B0CD, 0xECD5CC47, 0x6B72E6FD, 0x5FB337CB, 0xDC046235, 0xB3554069, 0x62E8D358, 0x2DBDEB7E, 0x736553EC, | |
0x0E465ED1, 0x009754A7, 0x9AD76638, 0x186AE66A, 0x8F34832E, 0xF4C54676, 0x4F5AC24D, 0x83734B08, 0x3E01D7ED, | |
0x31F830B6, 0x0B71C039, 0xF062BAFC, 0xC19CB1CA, 0x81A94E9B, 0x43F753CC, 0xAE467CB1, 0x3A24425D, 0x993840C2, | |
0x029E3F23, 0x189CEBD6, 0x30AE5F1F, 0x31C18967, 0x33009CD8, 0xF70963CF, 0x71B25C85, 0x9776E649, 0x1DC69634, | |
0x67C5F945, 0xDD8C3FC1, 0xA6B267CF, 0x67828F15, 0x258CCEAA, 0xDE7E40B0, 0x3FE203DB, 0x7F841970, 0x6F60AD42, | |
0x155E8ED0, 0x36CC984E, 0xB358111D, 0x82C7A44C, 0xF7D1361A, 0x4D0DD4EC, 0x9267C5FA, 0x5E0A7558, 0xCBED3CF6, | |
0xE43E5AE1, 0x7C3B1BB5, 0xE635509E, 0xA4B279FC, 0x1BFDA0F9, 0x9C3A46F9, 0xBF0A3982, 0x18999CE5, 0xFBB9999B, | |
0x5626E83B, 0xEC72FC45, 0xCF4EAB7E, 0xAB05621A, 0xA86466F0, 0x926F02E5, 0x0EA172C2, 0x882777AB, 0x490AE628, | |
0xDD8A4DA2, 0x2C934F7B, 0x88797186, 0x56D82195, 0x627D7C88, 0x045AF90D, 0x655118F9, 0x42F76C99, 0xF2122134, | |
0x022396CD, 0x25120833, 0xC6CD6F93, 0xAF7C08DF, 0x2DA99B63, 0x8EF8CF03, 0xB8098054, 0x4E9B2F5A, 0x022B0AEC, | |
0x1459055E, 0x02A0033F, 0xED67B9C8, 0x758057A5, 0xC7D8BA2A, 0xD4CC7CC6, 0x5F0B2597, 0x5AB84FFA, 0x496D1EE7, | |
0x8550FDA1, 0xDBBBDC70, 0x63149847, 0xC7CA2496, 0x96DBDCB7, 0xE2D4954A, 0xB9EC57F9, 0x6C70642C, 0x3D7B39F4, | |
0xF6161271, 0xE73A4943, 0x0EAA2FD6, 0xAB22A4BF, 0x134902F9, 0x1C4BA4DD, 0x558D617A, 0x8863374E, 0xC2EC82B0, | |
0x031A8ADE, 0x1741E8B1, 0x8F00A1CC, 0xF452F18F, 0x3A6E18D3, 0x6956DC4D, 0xDFA8EC1F, 0x69C52F20, 0x1ED99E2B, | |
0xEF7BAE7D, 0x7AF77378, 0x0B290733, 0x8C274A3E, 0x1F951C6C, 0xA3DDCEAC, 0x56F44ACB, 0x2270CE33, 0x9D874A9C, | |
0xF3A0F33E, 0xAFD74932, 0x2478581C, 0x551C9D3C, 0xAD063AA2, 0x31D17C9C, 0x88F7D6A0, 0x6DDD4F10, 0xDA0E114D, | |
0x8C2ABC96, 0x6FA83A7A, 0xE2452395, 0xA8219761, 0x620D783E, 0xAC489654, 0x3C1ACE7E, 0xC9C2A9BE, 0x7145AE6D, | |
0x4EF2ADDF, 0x53CA37A2, 0xA0A8A218, 0x67FD8F21, 0xBEAD8745, 0xB7711AD9, 0xD52B427F, 0x67ABBF1E, 0x0F66B464, | |
0xEB331E94, 0xADAAB204, 0x87756C23, 0x67F375BF, 0x54753FD8, 0x33ABC12D, 0x8F401EA1, 0x3C88D6FE, 0x615451C9, | |
0x87C32614, 0x268D494B, 0xF2AD7423, 0xCB949DA5, 0x25B4196E, 0xB2C5DF95, 0x8409721F, 0x0F7B5C12, 0x5E25EEEA, | |
0xC0F401B7, 0xA2DAEE3E, 0xF3AEAE52, 0x2A464F0D, 0x9CFB83EC, 0xF6E0EE51, 0x4774C554, 0x22DDFDE9, 0x5B599A74, | |
0x80EDBDE4, 0x2CC61BBD, 0xD824B10E, 0x2D0C3300, 0x99845362, 0xDEA64CE6, 0x575771AA, 0x961A3F14, 0x1432BEA6, | |
0x7D4FFF90, 0xF583772A, 0x4EE7C522, 0x07E4DEE6, 0x2C128C64, 0xD7D50924, 0x8223F310, 0x40BE7E09, 0x74DBC2E0, | |
0xBE3CDE01, 0x3E608447, 0xBD6A380E, 0xE5961202, 0xD34E32A0, 0x2539B5C0, 0x873A67C2, 0x239775F8, 0x1F9F60E1, | |
0xB63D3CF1, 0x30A5AF81, 0x8FD564FB, 0xA569DC35, 0x0D615EF8, 0xC49C2E07, 0xFBF7F35C, 0x9EDFEFF3, 0x148314D8, | |
0x8181CDF7, 0x7FA7653C, 0x5F40A6D5, 0xA994DB03, 0xBCCB55CC, 0x5D52D879, 0x65117BDD, 0x7D7F51D8, 0xB1BC1D10, | |
0x1F00F42E, 0x5C9957B7, 0x48C37C3B, 0x6F3D7E80, 0xC5158369, 0xF405690D, 0x49DACE68, 0xD2AC0D1D, 0xB399102A, | |
0x69F65B83, 0x324344F5, 0xA5D875EE, 0xBF2BD3F3, 0x2BB0CCCB, 0x7D6A05CF, 0x21AF29EB, 0x6367765B, 0xAD469391, | |
0xB1BCC75E, 0xC0518872, 0x94C52623, 0x1FB253E8, 0xAA314EB5, 0xCF2F792C, 0x00B08FF5, 0x90575FED, 0x16C1CF89, | |
0x2331EE19, 0x52590B8C, 0x06B4B6EC, 0xA46464C8, 0x955218F8, 0x6A75EFF8, 0xEEF53D04, 0x44650DB6, 0x03498691, | |
0xFF27365F, 0x4BAB9F2C, 0x97607DF2, 0xF831B2F7, 0x779EE348, 0xCF0D1F54, 0x6BA70606, 0x32C0B10C, 0xF33943ED, | |
0x31988090, 0x84B21458, 0x8701CC78, 0x632CF196, 0x0993A1D0, 0x55662BF3, 0x568FBC94, 0x76AE6160, 0x5FF57B9C, | |
0xE326F5C6, 0x161B30B8, 0x8132A32A, 0xAD3831C3, 0x032DDBA5, 0xFB836CDC, 0x2EC6CBF8, 0x6C831855, 0xEE8C0010, | |
0x5A64B2E3, 0xB3E9EC1B, 0xE6EAFBD0, 0xC1F2591A, 0x8E587584, 0x56398F78, 0x92DDB0C1, 0x1F76C224, 0x805FCD53, | |
0x74FF5EE9, 0xDC2FCEDA, 0x3E90D994, 0x15617A80, 0x4F1E077E, 0xB5DF16BF, 0x2854C143, 0x694E02C3, 0x4C3588AC, | |
0xCC7758A2, 0xA23959C6, 0x612647FF, 0xF2B95082, 0x1031E285, 0x42EFF0B4, 0xEFBCBD1F, 0x3499362D, 0xAD421535, | |
0x02911B94, 0x01CB816F, 0x0E274A1A, 0x7EDF8280, 0xADBD72AE, 0xDB20BBB3, 0x66CB4B73, 0xDE18190C, 0x6FEB4BA5, | |
0xEB719056, 0xEFAA7CFE, 0x100F8A13, 0x4E4AFD17, 0xD66DF5F1, 0xFB06B85D, 0x445AAFC0, 0x3B9F8385, 0x1B5330AF, | |
0xED70B42D, 0x2F2D81BC, 0x11873849, 0x5E65E5AB, 0xADF9C568, 0xACB45611, 0x59583575, 0xEB1C07F7, 0xB9E9BDF1, | |
0x65EB1D3D, 0xFA5FE526, 0x93C100A5, 0x2E414BC7, 0x7B0F062E, 0xCE77979B, 0x334965BB, 0x50BD7300, 0xE4273979, | |
0xC0EB2C14, 0x6E278874, 0x30523462, 0xF5D59CB2, 0xCA284788, 0xB84443BF, 0x1B7BDE26] | |
final = [0x9DDC359E, 0xF8288ABF, 0x9E1989CA, 0x59224ADB, 0xEFDEF866, 0xFC0BB7EB, 0x02D5C68A, 0xB3AC36F3, 0xDFBDAC75, | |
0x5F414DF0] | |
result = [0,0] | |
for n in range(5): | |
result[0] = deal_last_rev(final[2 * n]) | |
result[1] = deal_last_rev(final[2 * n + 1]) | |
result[0], result[1] = result[1], result[0] | |
result[0] ^= a4[16] | |
result[1] ^= a4[17] | |
for i in range(15, -1, -1): | |
v12, v11 = result[0], result[1] | |
result[0] = v11 ^ a4[i] | |
result[1] =v12 ^ ctypes.c_uint(a4[(v11 & 0xFF) + 786] + ( | |
a4[((v11 >> 8) & 0xFF) + 530] ^ (a4[((v11 >> 24) & 0xFF) + 18] + a4[((v11 >> 16) & 0xFF) + 274]))).value | |
print(str(binascii.a2b_hex(hex(rrev(result[0]))[2::]),encoding='utf-8'),end='') | |
print(str(binascii.a2b_hex(hex(rrev(result[1]))[2::]), encoding='utf-8'), end='') | |
# flag{W3lc0me_t0_Th3_Mu1lt1_Un1v3rs3!!!!} |
# blockchain
# 到国链之光一游
一道简单的区块链题目,去年 b 站 1024 程序员节的时候做了一道区块链,那一题的 wp 在这里,和这题考的知识点的关系应该是包含吧,这题考的知识点 b 站的那题也有,所以做起来当然是很轻松的,直接上攻击合约吧
contract Solve { | |
Greeter public greeter; | |
SignIn public signin; | |
uint signinTimestamp; | |
constructor(address _addr) { | |
greeter = Greeter(_addr); | |
signin = SignIn(greeter.startChallenge()); | |
signinTimestamp = block.timestamp; // 记录 SignIn 部署时间戳 | |
} | |
function solve() public { | |
bytes32 key = keccak256(abi.encodePacked(signinTimestamp)); | |
signin.getFlag(key); | |
} | |
} |